Introducing MAX — Take supply chain cyber risk management to the MAX

Your cybersecurity odyssey starts with trust
See the data that goes into your scores, and discover the methodology behind it
-
How we score
SecurityScorecard is the only company to provide complete transparency into our scoring methodology
-
Accuracy & attribution
A team of independent experts from Online Business Systems validated our methodology
-
Cyber insurance study
Marsh McLennan examined cybersecurity ratings’ correlation with reduced cyber insurance risk
Common questions
Ratings
- How are your cybersecurity ratings created?
SecurityScorecard ratings are created by: discovering the attack surface of an organization from the outside; picking up signals non-intrusively about that organization that indicate what’s happening inside the organization; and applying a statistical model that is based on nine years of historical data showing how organizations perform compared to others.
- Do I need to pay to access, improve, or challenge my SecurityScorecard rating?
Never. Any organization can access its scorecard for free and annotate it with internal information (such as SOC 2 documentation and compliance certifications) to ensure its voice is heard. In turn, we share recommendations with organizations on how they can improve their scores and become more resilient. This can all be done free of charge.
- Will I get breached even if I have an “A” rating?
Validation testing uncovered that companies with an A rating are 13.8X less likely to experience a breach than those with an F rating. But if a determined group of hackers or a nation-state decides to target an organization — even one with an A rating — it can get breached. Using the SecurityScorecard platform, customers can identify and plan for clear areas of improvement and thus reduce their cyber risk. Additionally, SecurityScorecard offers cyber resilience services such as Digital Forensics and Incident Response which can help you quickly triage a breach, stop further damage, investigate the source, and develop actionable reporting.
Data
- What is the frequency of your scans?
SecurityScorecard non-intrusively scans the entire IPv4 web space, more than 3.9 billion routable IP addresses, every 10 days across more than 1,400 ports.
- Do cybersecurity ratings only include outside-in data?
SecurityScorecard finds external-facing assets from the outside-in that can often indicate to an organization what’s happening on the inside, for instance: how diligently a browser’s operating system is patched, or the reaction time to malware. However, we also ingest inside-out info from organizations in order to provide more context into their internal security practices; organizations can list their security policies and provide documentation to support compliance with SOC 2, payment card industry (PCI) standards, HIPAA, and more. Organizations are also encouraged to submit questionnaires, claim profiles, and more.
- Do ratings take into account internal compensating controls?
While the visible Internet attack surface is the main target for cyberattacks—and generally a reflection of an organization’s cybersecurity posture—there’s a chance that there are internal vulnerabilities that we don’t see and aren’t represented in the overall score. However, SecurityScorecard calibrates our algorithms to account for this, and it’s why we allow any organization to provide additional context by contributing evidence of their internal security controls through internal security tools (such as XDR/EDR) integrations.
Accuracy
- If I think my score is inaccurate, what can I do?
SecurityScorecard offers a straightforward refute process that enables collaboration; is equally open to customers and non-customers; and encourages users to manage, validate, and make corrections as needed. If you believe your rating is inaccurate, our team is quick to respond with the industry’s fastest and most accurate refute process, while still maintaining credibility of the score.
- How long does it take to update my score?
After you submit a resolution or removal request, our customer support team will review the request and any supporting evidence within 48 hours. If your requests are approved by our support team, your new score will be reflected on your Scorecard as a Projected Score within a few minutes. If more action is needed, you will receive an explanatory email.
- Will my score be accurate if I own a small or medium-sized business (SMB)?
Our cybersecurity ratings are designed to find signals on any company, big or small; whether your organization has one IP address or one million. While there are enough signals provided by SMBs, there may be an overly positive perception of their security postures because their Internet attack surface is small. To increase accuracy, organizations should provide contributory evidence (such as: network designations, security policies, compliance validation, and more).
- Can I get an accurate score if I’m a cloud or telecommunications provider?
ISP/telecom providers have vast numbers of IP addresses. As a result, it can be difficult to attribute assets between their own corporate domains and the ones controlled by customers. Overall, this segment requires a more nuanced way of attribution. The security ratings industry is working on this challenge, and as the category advances we should see a more sophisticated approach to addressing this domain attribution issue.
Benefits
- How can I use ratings with my board of directors?
Use this template to communicate benchmarking, reduce supply chain risk, and prove the effectiveness of security investments. Download the template and make it your own.
- How can I use ratings to lower my cyber insurance?
Identify and plan for clear areas of improvement and reduce your cyber risk, which can result in validation with a higher security rating and, ultimately, a lower cyber insurance quote.
- How can I use ratings to monitor my third parties?
Obtain visibility into your cyber risk exposure by using security ratings to continuously monitor and measure the security posture of the third parties in your entire vendor ecosystem.




#SecurityDNA: Meet our CISO
Steve Cobb brings more than 25 years of leadership consulting surrounding IT infrastructure, cybersecurity, incident response, and cyber threat intelligence.
Read Latest BlogOur collaborative process
None of our users go it alone, and if you believe your score is inaccurate, we work with you to make it right. We offer a simple and fast corrections process that is equally open to customers and non-customers. We encourage users to validate and make adjustments as needed.
-


Claim your Scorecard
SecurityScorecard creates a Digital Footprint of all your organization’s Internet-facing assets. Discover critical security issues and assets you weren’t aware of, and improve your security posture.
-


Find a Public Scorecard
Public scorecards help vendor risk managers, information security professionals, procurement teams, and cyber insurers better understand security hygiene. Many organizations showcase their scorecard to build trust within their business ecosystem.
-


Show that you are trusted
Add a “Seal of Trust” to your website so your partners can easily see a snapshot of your security health. Each Badge features direct public access to a summary of why a company has a good score, along with real-time public visibility into how that security score has been maintained.
Transparency
Our customers have access to the greatest volume and quality of intelligence available. SecurityScorecard leverages data mined with the market’s leading capabilities, and relies on a global network of sensors to monitor signals across the internet. We enrich our data using commercial and open-source intelligence sources, and track over 79 security issues.
Learn More About Our Transparency
| NUMBER OF SECURITY ISSUES DISCOVERED |
The data that powers the SecurityScorecard platform
Customers choose SecurityScorecard because the depth of our data is unmatched. And our ability to validate that data increases with every new customer and follower. In order to make our security ratings as meaningful as possible, we conducted a study using machine learning-tuned issue-type weights, and found that organizations with an A rating are 13.8x less likely to sustain a breach than those with an F rating.
The industry’s largest data set
With millions of companies scored, the depth and scope of our collected data is unmatched, and our ability to validate our data increases with every new customer and follower. These numbers are updated in real time, and illustrate the expansive reach of our scoring and monitoring.
| COMPANIES RATED
|
UNIQUE COMPANIES FOLLOWED
|
-
Hear why our customers and partners trust us
At SecurityScorecard, we work closely with our partners and customers, whose insights influence our roadmap. Whether it’s sharing input on new offerings and services or helping us troubleshoot issues, every piece of feedback is an opportunity for us to do better.
Industry Recognition
-
Metrics
Live metrics on our performance, in addition to overall statistics, corrections, response times, and ratings stability.
SecurityScorecard commissioned a team of independent pentest experts to audit a sample of Scorecards to objectively determine the accuracy of our IP and domain attribution. The accuracy for positively attributing IP Addresses was found to be 94%, and for DNS Records it was found to be 100%.

Independent accuracy verification


-
"The accuracy for positively attributing IP Addresses was found to be 94% while for DNS Records it was found to be 100%."
SecurityScorecard commissioned an independent report to study the accuracy of our attribution1 / 0
Refutes and accuracy
Any rated entity can challenge their digital footprint or any of the measurements we provide on it, whether they are a customer or not.
To demonstrate our scoring accuracy, these charts show the fraction of our findings that are refuted.
These accuracy metrics are based on the number of assets or findings refuted compared to the number of assets or findings for the entities that are refuting. For example, if 10 companies each refute 10 domains (100 domains in total) and these 10 companies have 1,000 domains each (10,000 domains in total), then the refute rate is 1% (number of domains refuted/number of domains).
We show a trailing 7 day average to make the data easier to interpret.
Response times and findings
| REFUTE RESPONSE TIME
|
FINDINGS REFUTE RATE
|
Digital footprint metrics
| IP MISATTRIBUTION RATE
|
DOMAIN MISATTRIBUTION RATE
|
Principles
In 2017, SecurityScorecard and more than two dozen other companies joined the U.S. Chamber of Commerce to establish a set of Principles for Fair and Accurate Security Ratings. These principles were created to increase confidence and transparency in security ratings. View the Principles
Transparency
This means: explaining how we calculate cybersecurity ratings, how we attribute IPs and domains to entities, make measurements, and score findings.
The vast majority of all the data we use for digital footprints and scoring is gathered through our own proprietary collection methods. We use very little OSINT (Open Source INTelligence) data and we only buy small amounts of data from other sources.
Users must be able to verify our attribution and findings. As an example, for SPF findings, we display the information we believe users need to find and fix the issue; the SPF issue itself, the domain the issue was seen on, and the last date the issue was observed.
Visit the Methodology section for more information about our scoring process and data collection >
Dispute, correct, and appeal
We provide a mechanism to dispute our findings, as well as IP or domain allocation. We also accept compensating controls which users put in place to mitigate findings; for example, managing the threat of a CVE.
Visit the Corrections section to read more about the dispute process. >
Visit the Metrics section to learn more about our accuracy and to find out how long we take to resolve issues. >
Accuracy and validation
According to the U.S. Chamber of Commerce principles, cybersecurity ratings companies should provide validation of their methodologies and historical performance of their models.
SecurityScorecard commissioned a team of independent pentest experts to audit a sample of Scorecards to objectively determine the accuracy of our IP and domain attribution. The accuracy for positively attributing IP Addresses was found to be 94%, and for DNS Records it was found to be 100%.
Read the report here. >
Visit the Methodology section to read more about our validation. >
Visit the Metrics section to see the historical performance of our models. >
Model governance
The stability of our ratings is important to our users and to us. Normally, we provide 30 days or more advance notice of changes. However, occasionally there are acute threats (such as Log4j or OpenSSL 3.07) where we may introduce changes more rapidly.
Prior to releasing changes, we test for impact and we include customer-facing staff in our release process.
Independence
Every entity is scored in the same way, regardless of whether they’re a customer or not.
We respond to disputes regardless of whether they originate with a customer, a freemium user, or anyone else.
The presence or absence of commercial agreements does not impact our cybersecurity ratings or our dispute process.
Confidentiality
We do not publish or otherwise distribute information that could aid bad actors or that could lead to a system compromise. We follow responsible disclosure rules.
Methodology
An overview of how security ratings are calculated. Read about our scoring methodology in greater detail:
-

Domains and IP addresses are allocated to companies using data from multiple sources, but primarily from our own scanning and data collection activities. This information is refreshed and revised daily.
-


Measurement data is collected from the Internet, including, but not limited to: bot infections, CVEs, SPF and DMARC configurations, out-of-date browsers and operating systems. We gather almost all this data ourselves.
-


Measurements are then allocated to companies using our domain and IP mappings.
-


Measurements are scored based on their severity, i.e., their likely contribution to breaches.
-


Related scored measurements are aggregated into factors (such as Network Security), and these factors are combined into a total score using weightings. These weightings represent the relative likelihood of breach for each factor.
-


We review our scoring methodology constantly, which means our IP and domain attribution methods, our measurements, and our scoring algorithm.
-


The stability of our ratings is important to our users and to us. In most cases, we give advance notice of changes that affect scores, though when an acute risk arises (e.g. Log4j) we may make changes more quickly.
-


Prior to releasing changes, we test for impact and we include customer-facing staff in our release process.
About our data
Learn moreHow we collect data
We have our own attribution and threat intelligence teams, who source almost all of the data we use (97%).
While this data is theoretically available to everyone, in practice one would need bespoke collection systems, special skills, or trusted access. Good examples are dark web access, internet scanning data, or bulk DNS records; there are no free repositories of this kind of data. In effect, this means the data is not “publicly” available.
We buy small amounts of data from third parties, and we use even smaller amounts of OSINT (public “open source”) data.
All of the data we use is ethically and lawfully obtained. We only collect data on entities, not on people.
How we score our findings
Each finding is assigned a weight; the more serious the finding, the higher the weight it gets. We assign higher weights to findings that are more strongly correlated with breaches.
Learn more about our scoring methodology in this scoring whitepaper.
How we validate our findings
We use multiple mechanisms to check our data quality:
- We monitor corrections from our users, which we aim to keep below thresholds.
- We look for patterns in corrections to deal with any underlying issues.
- We spot check attribution and findings data.
Users need to validate that our findings, as well as our IP and domain attributions are accurate.
Scoring and attribution changes
In most circumstances, we will provide advance notice of changes, for example, we might introduce a new finding type as informational (unscored) some time prior to scoring it. Or we may provide a grace period before we score findings. However, in some cases we may introduce immediate scoring changes based on acute threats (such as Log4j.
Before changes are released, they go through a Change Control Board and undergo impact assessments.
For our major releases, we provide release notes on what the changes were. Read these release notes here: Release notes
The data that powers the SecurityScorecard platform
Customers choose SecurityScorecard because the depth of our data is unmatched. And our ability to validate that data increases with every new customer and follower. In order to make our security ratings as meaningful as possible, we conducted a study using machine learning-tuned issue-type weights, and found that organizations with an A rating are 7.7x less likely to sustain a breach than those with an F rating.
-
SCORING
SecurityScorecard provides A-F rating across 10 risk factor categories, including: application security, DNS health, endpoint security, and patching cadence). The aggregated information is summarized based on a standard 0 to 100 measurement metric that maps to a simple color-coded letter grade. The highest letter grade is an “A,” which indicates a low number of recent security issues, followed by “B,” “C,” “D,” and “F,” as the number of threat indicators increases.
-
DATA SOURCES
Our data sources include:
- IP addresses
- Exposed port mappings
- Fingerprints of services, products, libraries, operating systems, devices, and other internet-exposed resources, including version numbers
- Common Platform Enumeration (CPE) IDs
- Common Vulnerability Enumeration (CVE) Version 2 IDs
- Script output from Nmap, the open-source scanner that is one of the components of our own scanning framework.
-
SCANNING
We have built and maintained our own scanning infrastructure and collect 97% of our own data. We scan 4.1B IPs every 1.5 weeks across 1,400 ports globally, with honeypots in over 65 countries and 120 distinct sensors that grab hundreds of millions of active attacks every day. All of this enables us to continuously monitor over 12 million organizations, track over 10,000 high severity CVEs, and detect over 100 Billion vulnerabilities and attributions each week.
-
SIGNALS
SecurityScorecard monitors signals across the internet, using a network of sensors spanning three continents. Additionally, we operate one of the world’s largest networks of sinkholes and honeypots to capture malware signals and further enrich our data set with commercial and open-source intelligence sources. We supplement our data collection with external feeds from public and commercial data sources. These additional data-gathering methods help produce issue types related to leaked data.
The industry’s largest data set
With millions of companies scored, the depth and scope of our collected data is unmatched, and our ability to validate our data increases with every new customer and follower.
These numbers are updated in real time, and illustrate the expansive reach of our scoring and monitoring.
COMPANIES RATED
|
|
Why this matters to you
Why this matters for you: The more companies we rate, the more accurate we get. Our platform processes more data than any other security ratings platform, and our algorithms provide more meaningful correlations between signals and breaches. |
UNIQUE COMPANIES FOLLOWED
|
|
Why this matters to you
From industry, location, or company size, a greater variety of companies in our data repository improves the accuracy of our ratings, so you can make better security decisions. |
USERS LOGGED IN TODAY
|
|
Transparency
Our customers have access to the greatest volume and quality of intelligence available. SecurityScorecard leverages data mined with the market’s leading capabilities, and relies on a global network of sensors to monitor signals across the internet. We enrich our data using commercial and open-source intelligence sources, and track over 79 security issues.
NUMBER OF SECURITY ISSUES DISCOVERED
|
|
UNIQUE COMPANIES FOLLOWED
|
|
|
|
|
|
Incidence of cybersecurity flaw vs. digital footprint
SecurityScorecard’s scoring algorithm is based on a principled statistical framework.
One of the biggest challenges to providing fair cybersecurity ratings is properly accounting for company size. Attack surface typically scales with digital footprint, which ranges from a single IP for a small company to hundreds of millions of IPs for a large tech firm. To level the playing field, SecurityScorecard measures how the incidence of cybersecurity flaws (i.e. number of issue findings) varies with company size, and evaluates companies compared to organizations of similar size.
The number of findings for exposed Microsoft’s Remote Desktop Protocol (RDP) service vs. the number of IPs (size of digital footprint).
                              |
KEY:Dashed blue line: Corresponds to the average incidence (no. of findings). For example, an organization with 106 IPs (i.e. 1,000,000 IPs) typically has about 102 (i.e. 100) findings for exposed RDP service. Blue dots: Each blue dot corresponds to a scored company. Yellow band: Organizations in the yellow band receive an average score. Green band: Companies in the green region (fewer than average findings) receive a better score. Red band: Those in the red region (worse than average findings) receive a worse score. |
How we collect our data
We have our own attribution and threat intelligence teams, who source almost all of the data we use (97%).
While this data is theoretically available to everyone, in practice one would need bespoke collection systems, special skills, or trusted access. Good examples are dark web access, internet scanning data, or bulk DNS records; there are no free repositories of this kind of data. In effect, this means the data is not “publicly” available.
We buy small amounts of data from third parties, and we use even smaller amounts of OSINT (public “open source”) data.
All of the data we use is ethically and lawfully obtained. We only collect data on entities, not on people.
Corrections
None of our users go it alone, and if you believe your score is inaccurate, we work with you to make it right. We offer a simple and fast corrections process that is equally open to customers and non-customers, in accordance with the US Chamber of Commerce guidelines. We encourage users to validate and make adjustments as needed. How to update your Digital Footprint. View the step-by-step instructions below.
VIEW THE US CHAMBER OF COMMERCE GUIDELINESSTEP 1
Log in to your account
- If you do not have an account, you can sign up for a free one here.
- Once you’ve signed up, claim your Scorecard.
STEP 2
Navigate to the IP address or domain you’d like to refute, then select the items in the check box.
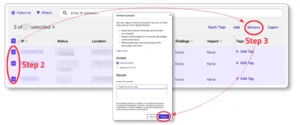

STEP 3
Click the “Remove” text on the top right.
You should then see the “Remove assets” dialog:
Fill in the dialog and click the “Remove” button.


How to resolve an issue finding Here’s the step-by-step process:
Read more about the issue resolution processSTEP 1
Navigate to the issue type you want to refute
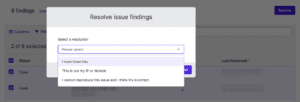



STEP 2
Elect the findings you want to refute on the left hand side of the dialog




STEP 3
Click the “Resolve” button.




Compliance and Regulatory Information
SecurityScorecard is trusted by public sector agencies, financial regulators, and industry groups. We’re committed to maintaining data privacy and compliance for our customers, partners, and vendors.
-
SOC 2
We have successfully completed AICPA SOC 2® examinations since March 31st, 2019 and we’re currently SOC 2 certified. If you’d like to see our SOC 2 documentation, please contact us.
-
Compliance with export regulations
We comply with applicable US and international laws and regulations on export controls.
-
Compliance with applicable privacy laws and regulations
SecurityScorecard is committed to the privacy of our customers and complying with all applicable privacy laws. We pick up signals non-intrusively about an organization’s digital footprint. For detailed information on our privacy practices, please review our Privacy Policy.
-
About our systems
We do not maintain our own cloud servers. Instead we buy in-cloud computing services from other vendors, most notably AWS. We use AWS in the United States to process ratings data and store and process customer data.
Cooperation with regulators and trade organizations
-
NYDFS
The New York Department of Financial Services (NYDFS), uses our ratings to monitor its regulated entities
-
CSA
Cloud Security Alliance (CSA) members have access to a SecurityScorecard Enterprise License, which gives them the ability to benchmark themselves against the CSA Cloud Controls Matrix (CCM).
-
JCDC
SecurityScorecard has partnered with the Joint Cyber Defense Collaborative (JCDC) to share cyber threat information in defense of public and private critical infrastructure.
-
CSBS
The U.S. Conference of State Bank Supervisors (CSBS) provides state financial regulators with access to SecurityScorecard’s cybersecurity ratings platform and connected services.
-
CISA
The U.S. Cybersecurity and Infrastructure Security Agency (CISA) added SecurityScorecard to its catalog of Free Cybersecurity Services and Tools.
-
DHS
SecurityScorecard’s Attack Surface Intelligence solution has been added to the Department of Homeland Security (DHS) Continuous Diagnostics and Mitigation (CDM) Program’s approved products list (APL).
Active Memberships
-
CYBER THREAT ALLIANCE
SecurityScorecard is an active member of the Cyber Threat Alliance
-
WEF
Part of the World Economic Forum’s (WEF) global innovators community.
-
ISACS
SecurityScorecard is proud to support 14 industry Information Sharing and Analysis Centers through our ISAC Partner Program.
Privacy
SecurityScorecard is committed to the privacy of our customers and complying with all applicable privacy laws. For detailed information on our privacy practices, please review our Privacy Policy.
-
Non-Intrusive
Ratings are non-intrusive. Data we collect is all publicly observable from the open Internet.
-
Digital Footprint
SecurityScorecard picks up signals non-intrusively about an organization’s digital footprint.
-
Observable Data
Scans the entire IPv4 web space, and collect publicly observable data.





